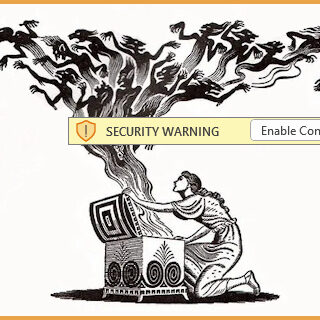
Do not enable content
Consider the following situation: Someone you’ve communicated with before sends you a personalized but unsolicited email with an attachment. You check the return email and confirm that it came from the person’s legitimate email address. Even though you were not expecting the email, you open the attachment anyway. The Microsoft Office document prompts you to…